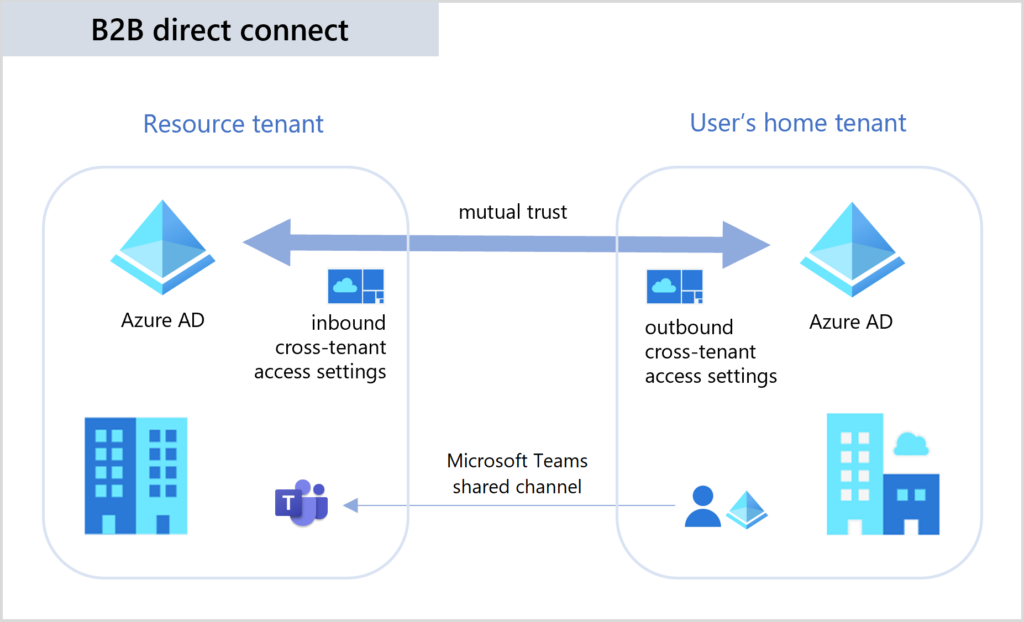
External collaboration in shared channels is powered by B2B direct connect, a new way to collaborate with other Azure AD organizations—no need to add the external user as a B2B guest. Azure AD admins can manage B2B direct connect using cross-tenant access policies. External collaboration is off by default. To enable a shared channel between organizations, both sides must configure cross-tenant access policies. Admins can grant, restrict, or revoke access for external users at an individual, group, or tenant level.
PLEASE note – everything requires settings to be correct in BOTH tenants – meaning both in your home tenant and in the guest tenant, or the tenant where you should act as guest.
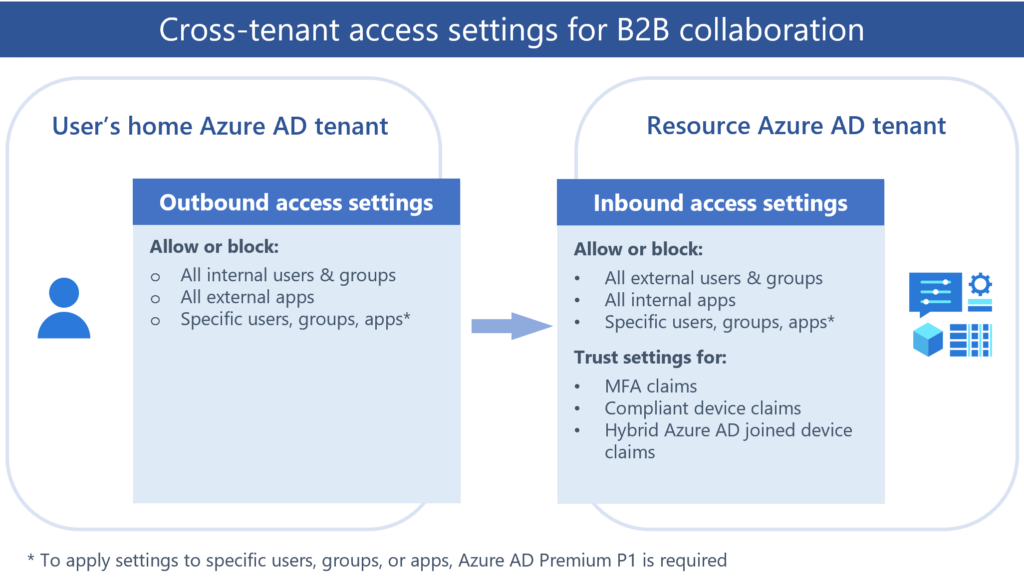
Settings are divided between Internal and External settings – its important to know the difference.
- Inbound access settings control whether users from external organizations can access resources in your organization. You can apply these settings to everyone, or you can specify individual users, groups, and applications.
- Outbound access settings control whether your users can access resources in an external organization. You can apply these settings to everyone, or you can specify individual users, groups, and applications.
Make a note, that to use the ability to block or allow specific users or groups, Azure AD premium P1 is required
So far so good, lets get some real world examples.
EXAMPLE 1 – We want to enable this feature but limit for specific external companies.
So out of the box – this preview feature comes disabled.
So to turn it on at all, you need to go to the Azure portal and Find “Azure Active Directory”
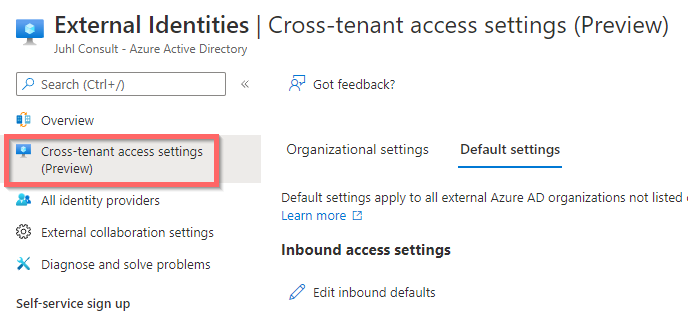
Now click “Edit Inbound defaults” to open up for inbound access.
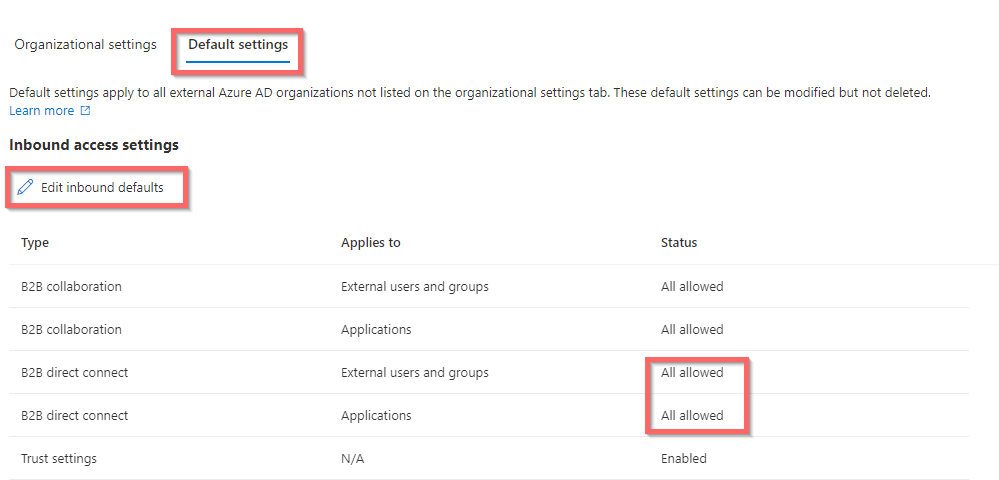
And do the same for “Edit Outbound details”
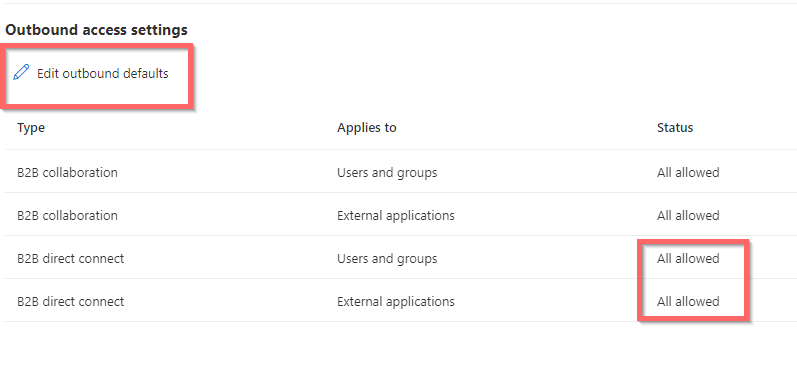
The settings must look like this:
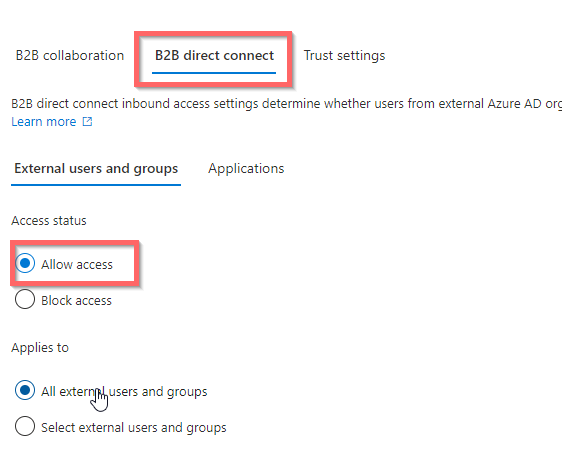
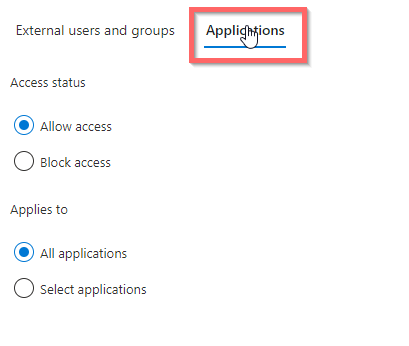
So now ALL users can share and collaborate with all Users and Groups in all external Azure AD Tenants. !
So here is how to block specific organizations:
Leave the defaults as is, and the go to “Organizational settings” still in Cross-tenant access
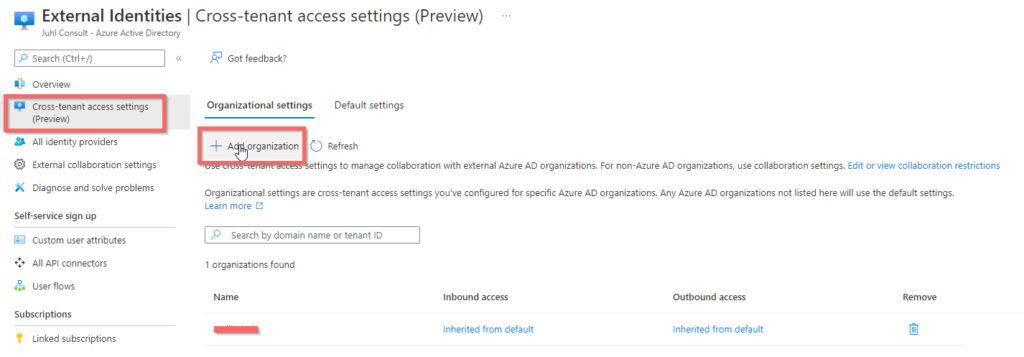
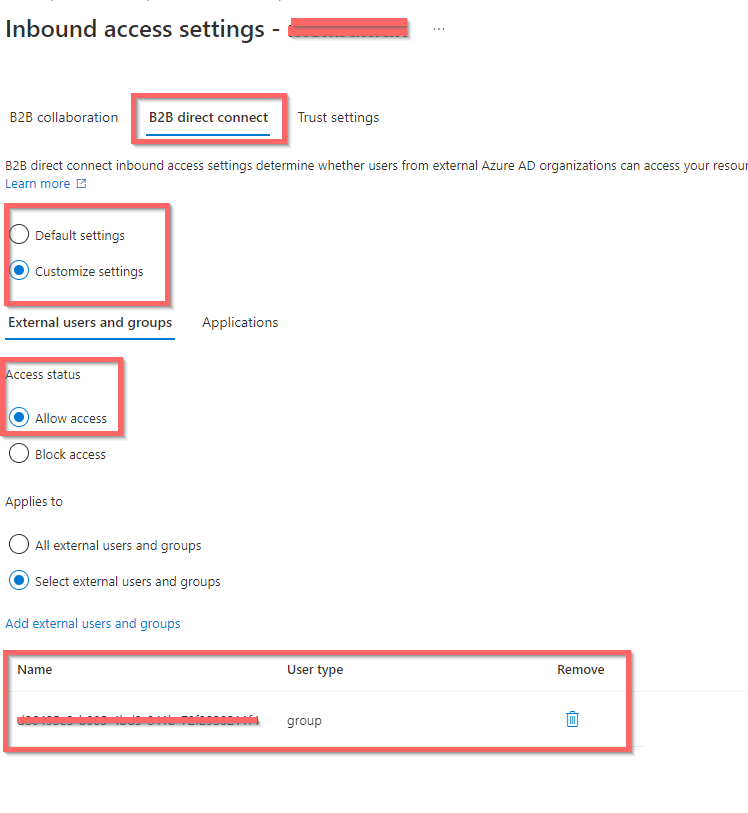
Click “Add organization” and search by use of domain name, or tenant ID. It will ask to copy defaults, do that, and then narrow down from there, It is possible to Block or Allow the following:
- Whole tenant
- Single User
- Specific group (Team)
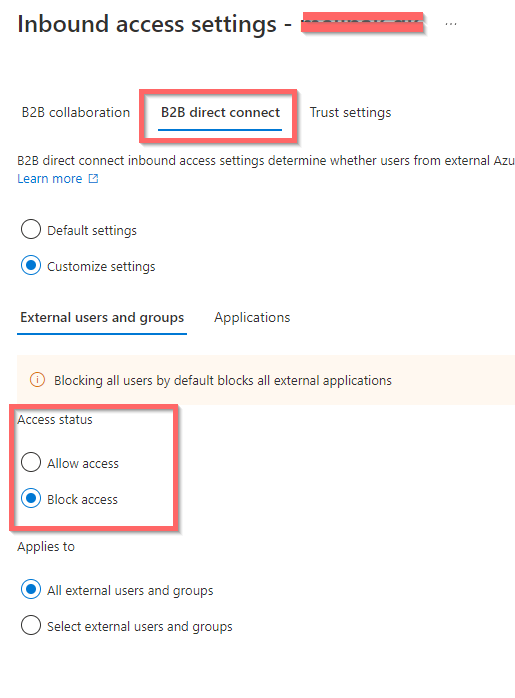
Now access is allowed for ALL tenants – except the one(s) specified in Organizational settings.
EXAMPLE 2 – We want to disable this feature but allow for specific external companies.
So the other way around – if you did not touch the settings yet, you can skip the next couple of steps to change the default to block, its already there.
Otherwise – start by setting defaults, for botth inbound and outbound.
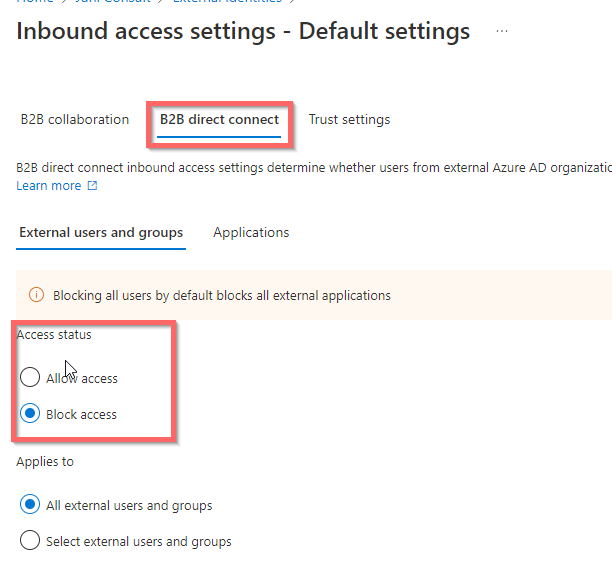
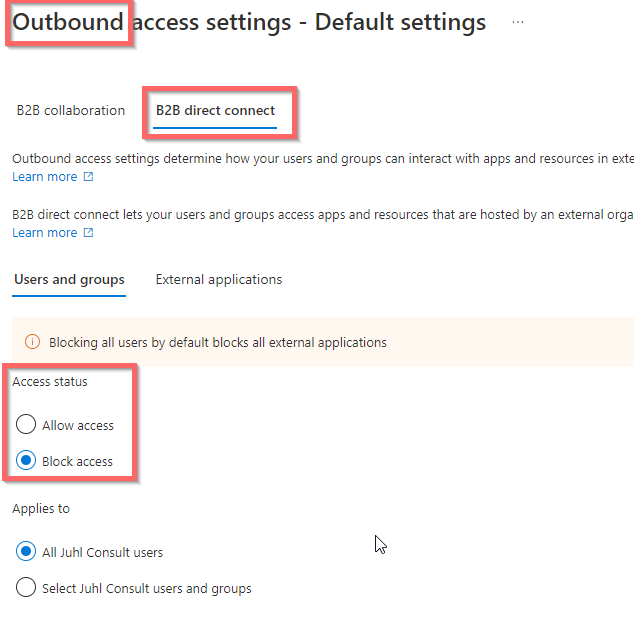
Now all is blocked and we can – just like before – add a single or multiple external tenants into Organizational settings

Again you will notice newly added orgs, inherit the settings.
Now again we can narrow the allow list down as far as:
- Whole tenant
- Single User
- Specific group (Team)
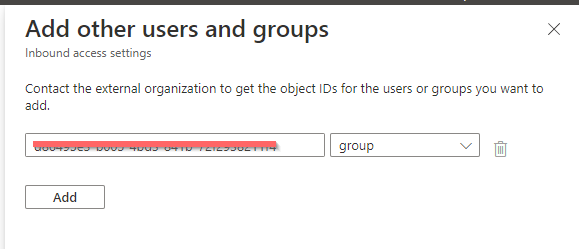
Add specific users or Teams (groups) by GUID and choose the individual settings.
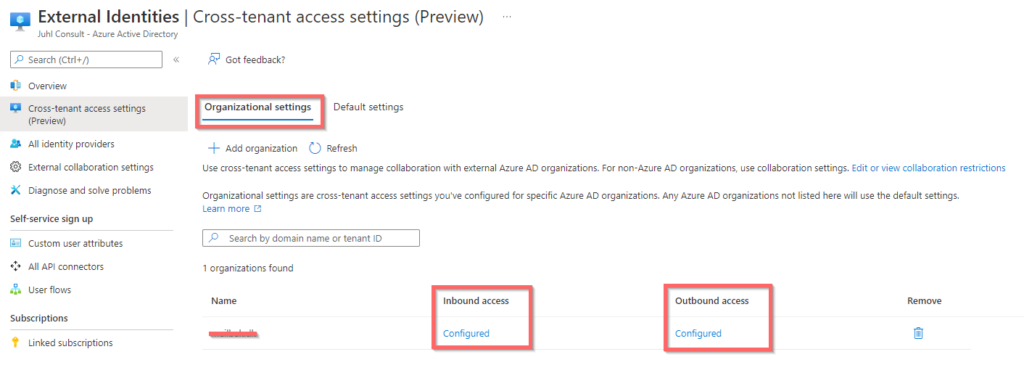
Look at theese resources for more info:
General info: https://docs.microsoft.com/en-us/microsoftteams/shared-channels
Cross-Tenant access: https://docs.microsoft.com/en-us/azure/active-directory/external-identities/cross-tenant-access-overview
Have a great rest of your day 🙂


